Have you ever stopped to think about workflow audit trails the secret digital breadcrumbs that trail behind your every move within the intricate labyrinth of technology?
Today, we’re embarking on a journey to unravel the enigma of workflow audits—those fascinating, behind-the-scenes records that illuminate the inner workings of our digital universe.
Picture this as a virtual adventure where each tap of a keyboard or click of a mouse leaves a mark, akin to footprints in the sand.
Intrigued? Well, get ready to explore the world of audit workflows, the unsung heroes of transparency and security in our digital age.
Article Outline
Why Workflow Audit Process Matters
The idea of a workflow audit trail might seem like a subplot from a high-tech thriller in a world where data rules and information flows seamlessly through networks and systems.
But let me assure you, it’s far from fiction. It’s the map that charts the course of actions within processes and systems, leaving no room for ambiguity or guesswork. So, why should you care?
Peering into the Invisible Threads
Imagine this: You’re the director of an intricate play, and the stage is set with multiple actors, each playing their part. But what if you need to know who moved that prop, when the spotlight shifted, or who ad-libbed that unexpected line?
Enter the workflow audit trail. It’s your backstage pass, granting you access to a timeline of every action, every modification, and every interaction. But why is this invisible thread of actions so crucial?
In a world where trust and transparency reign supreme, audit documentation serves as the digital equivalent of a trust fall. They act as your watchful eye, recording each step taken, every change made, and every access granted.
But why is this important? Hold on tight, because the benefits are about to hit you like a breeze.
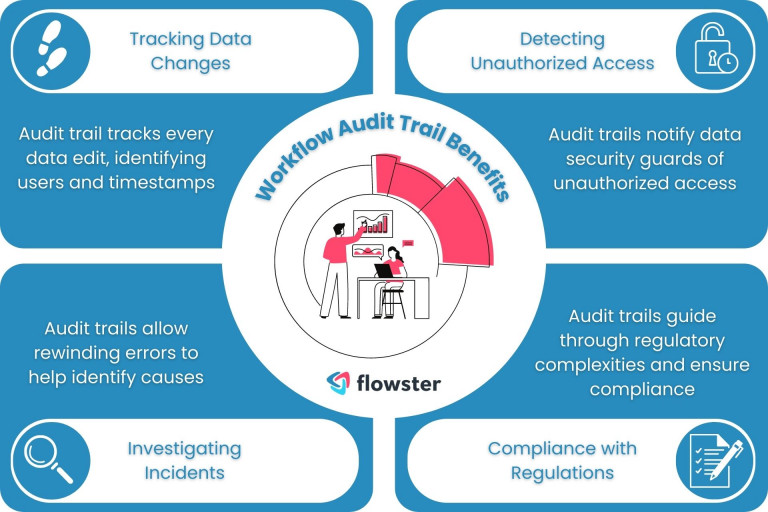
Audit trails play a critical role in tracking changes, identifying unauthorized access, investigating incidents, and ensuring compliance with regulations within digital processes.
How Having an Audit Workflow Can Help You
Now, let’s dive into the treasure trove of benefits that audit trails bring to the table:
- Tracking Changes to Data: Consider your data as a canvas, and each edit as a brushstroke. With an audit trail, you can track each stroke, documenting who held the brush and when the masterpiece evolved. No more wondering, “Who turned my Mona Lisa into a Picasso?”
- Identifying Unauthorized Access: Imagine your data as a secret vault. Audit trails stand guard, alerting you if anyone tries to pick the lock. It’s like having a personal security detail for your digital assets.
- Investigating Incidents: Accidents happen, and sometimes the spotlight flickers. With an audit trail, you can rewind the scene and analyze every action leading up to the mishap. It’s your digital rewind button, helping you uncover the mystery behind unexpected errors.
- Complying with Regulations: Ah, the dreaded labyrinth of regulations. Fear not! Audit trails act as your trusted guide, ensuring you’re not lost in the maze. They keep your actions transparent, making sure you’re always in line with the rules of the game.
So, you see, audit trails aren’t just lines of code; they’re the guardians of accountability, the sentinels of security, and the torchbearers of transparency in the digital age.
But what exactly makes up these audit trails, you ask? Let’s dive deeper into the components that make them the superheroes of the tech world.
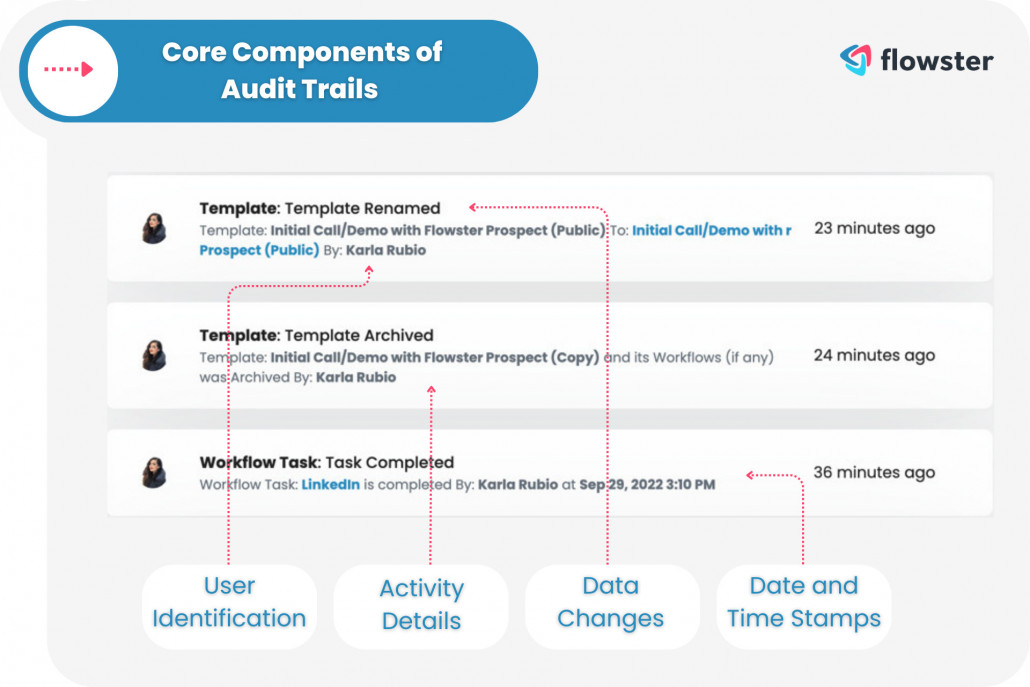
The Parts of a Workflow Audit Trail
So, we’ve embarked on this quest to understand the magic behind workflow audit trails. Imagine these trails as a well-kept journal chronicling every interaction and event within the digital realm.
Now, let’s flip through the pages and unveil the fascinating components that bring these audit trails to life.
Date and Time Stamps: The Timestamp Chronicles
Consider this: every action you take within a system has a timestamp, like a little note jotted down in the margins of your digital diary. These timestamps are crucial for recreating the timeline of events.
Just like a detective needs to know when a crime occurred, an audit trail relies on date and time stamps to piece together the sequence of actions. It’s like having a time-traveling companion who always knows when things happen.
User Identification: The Cast of Characters
Ever watched a movie without knowing who the actors were? An audit trail doesn’t make that mistake. It introduces us to the protagonists behind every action.
User identification is like the opening credits, revealing the personas responsible for the actions recorded. Whether it’s a system administrator, an enthusiastic intern, or the elusive guest user, the audit trail assigns roles to each player in the digital theater.
Activity Details: The Scene Descriptions
Now, let’s zoom in further. For every action captured in the audit trail, there’s a detailed description—a scene painted with words. It answers the “what” of the action. Did someone edit a file? Delete a record? Upload an image?
These activity details provide context, offering a glimpse into the nature of the event. It’s like reading a well-crafted scene description in a script—you instantly know what’s happening.
Data Changes: The Evolution of Content
Imagine tracking the evolution of a character in a story. In the same way, audit trails follow the journey of data. If data is the protagonist, the audit trail is its character arc.
It documents changes made to the data, whether it’s a slight alteration or a significant transformation. It’s your backstage pass to the data’s growth, capturing each twist and turn in the narrative.
Workflow Audit Trails Unlock the Power of Transparency
As we peel back the layers of the audit program, it becomes evident that this seemingly complex concept is rooted in transparency and accountability. Just as a well-written book reveals its secrets through carefully placed clues, audit trails offer insight into the intricacies of digital actions.
They’re the threads that connect the dots, allowing us to retrace our steps, analyze events, and ensure the integrity of our digital landscapes.
It’s intriguing, isn’t it? We’ve only scratched the surface of the intricate world of workflow audit trails. These components, working harmoniously, create a symphony of accountability and transparency.
But how do you actually create this symphony? How do you weave these components together to compose a comprehensive workflow audit trail?
Buckle up as we delve into the realm of creating and managing these digital chronicles, turning mere interactions into a captivating narrative of actions and outcomes.
Making Your Own Audit Trail Adventure
Alright, it’s time to put on your audit trail hats and become the architects of your own digital journeys. Creating an audit trail might sound like something straight out of a sci-fi flick, but fear not—it’s all about methodical planning and a touch of digital magic.
Let’s roll up our sleeves and dive into the art of crafting your very own audit trail adventure.
Step 1: Choose Your Battles
Imagine this: You’re a curator at an art gallery, carefully selecting pieces for an exhibition. Similarly, you need to decide which actions within your digital domain warrant a spot in your audit trail.
Not every brushstroke needs to be recorded; focus on the crucial actions that tell the story. Think of it as curating a collection of significant moments.
Step 2: Detail Level Dilemma
Remember Goldilocks and her quest for the perfect porridge? When it comes to audit trails, finding the right level of detail is your Goldilocks moment.
Too much detail overwhelms, while too little leaves gaps in the narrative. Strike a balance that captures enough information to tell a clear story without drowning in unnecessary data.
Step 3: The Collection Method Magic
Now comes the technical bit. How do you actually gather the data for your audit trail? It’s like collecting puzzle pieces that fit seamlessly together.
You might use specialized software or even custom-built solutions to capture and store the data. Think of it as assembling your toolkit—the tools you’ll need to craft your audit trail masterpiece.
Step 4: Fortifying Security
Just like protecting a precious artifact, your audit trail data deserves top-notch security. Implement measures that safeguard this digital diary from prying eyes.
Encryption, firewalls, and access controls are your knights in shining armor, ensuring that only authorized individuals can access and decipher the trail’s secrets.
Creating your own audit trail adventure isn’t just about following a set of steps; it’s about weaving a narrative of transparency and accountability. Think of it as crafting your own digital novel, where each action is a chapter and each detail adds depth to the plot.
So equip yourself with the knowledge and tools needed to embark on this journey. The world of audit trails is waiting, and it’s time to leave your mark on its pages!
Transform Your Business Processes with Flowster's AI-Driven Automation
How to Get Good at Managing Audit Trails
Now that we’ve ventured into the realm of crafting audit trails, it’s time to delve deeper into the art of mastering their management.
Think of it as keeping your novel well-organized and captivating from start to finish. So, grab your magnifying glass and detective hat as we uncover the secrets of becoming an audit trail virtuoso.
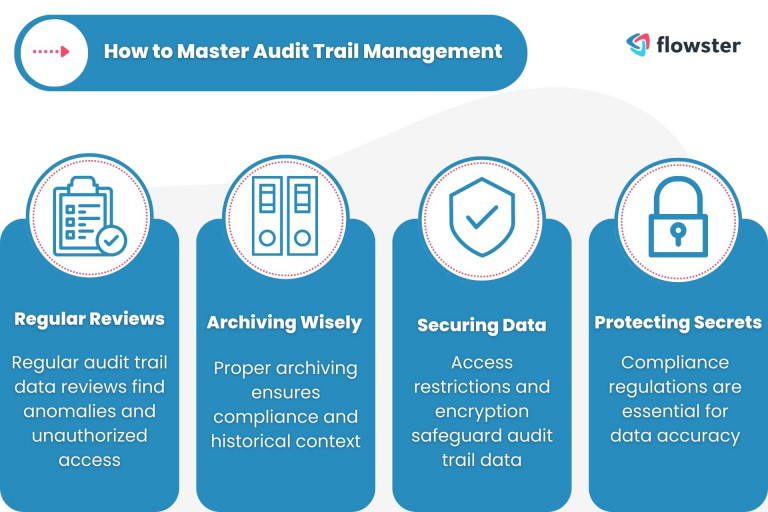
Regular Reviews: A Sherlock Approach
Remember how Sherlock Holmes meticulously analyzed clues? Apply the same method to your audit trail. Regularly review the data to spot any irregularities or suspicious activity.
It’s like checking your bank statements for unfamiliar transactions—any anomaly should trigger an investigation. This proactive approach ensures that you’re always one step ahead of potential issues.
Furthermore, previously developed workflows from older audit processes must be reevaluated and redefined to fit the current process.
Archiving Wisely: Chronicles of Time
Every tale needs an archive, and so does your audit trail. But don’t toss it aside too soon. Regulations often dictate how long you should keep your records.
Think of it as preserving historical documents; they’re a window into the past. Keeping your audit trail data for the required duration ensures compliance and provides valuable context for future analysis.
Securing Your Treasure: Guardians of the Vault
Imagine the vault that holds a king’s riches—that’s how you should treat your audit trail data. Guard it fiercely! Only authorized personnel should have access to this treasure trove.
Implement access controls, granting entry only to those with a rightful claim. Multi-factor authentication adds an extra layer of protection, ensuring that only the chosen ones can unlock the vault.
Protecting Secrets: Encrypting the Saga
In a world of digital intrigue, encryption is your most potent spell. It transforms your audit trail into an unreadable code for anyone without the key. It’s like writing in a secret language only a select few can decipher.
Encryption shields your data from unauthorized access, ensuring that even if someone gains entry, they’ll be met with an impenetrable barrier.
As you embark on your journey as an audit trail maestro, remember that you’re not just managing data; you’re safeguarding your digital legacy. With regular reviews, careful archiving, stringent security measures, and unwavering compliance, you’ll be well-equipped to face the challenges that lie ahead.
Maintaining Compliance: Navigating the Regulatory Maze
As we journey through the intricacies of audit trail management, there’s a crucial station we must not miss: the Compliance Junction.
Imagine this as a crossroads where rules, regulations, and responsibilities intersect. In this chapter, we’re donning our explorer hats to decipher the map of compliance, ensuring our audit trail journey stays on the right track.
Safekeeping in Secure Vaults
Imagine your audit trail as a precious artifact—the crown jewel of your digital realm. Just as you’d entrust the jewels to a secure vault, your audit trail data must be stored in a similarly fortified environment.
Think of it as placing your treasure beyond the reach of potential intruders. This vault could be a dedicated server or a cloud-based storage solution designed to keep your data under lock and key.
Access Granted to the Chosen Few
A knight wouldn’t hand over their sword to just anyone, right? Similarly, your audit trail data should only be accessible to those with a legitimate claim. Implement access controls that grant entry only to authorized individuals.
It’s like a secret chamber accessible only to those with the right credentials. By restricting access, you ensure that only the designated personnel can journey through the audit trail’s narrative.
The Encryption Enigma: Concealing Secrets
Imagine your audit trail as a message in a bottle, cast adrift in a sea of data. Encryption is the secret code that keeps that message safe from prying eyes. It’s like writing your message in a language only those with a decoder can understand.
By encrypting your audit trail data, you create a barrier that shields it from unauthorized access. Even if someone manages to access the data, they’ll find it incomprehensible without the key.
The Dance of Compliance Regulations
Navigating compliance is like mastering a complex dance routine; it requires finesse and precision. Depending on your industry and region, there might be specific regulations dictating how you should manage your audit trail data.
Think of these regulations as the choreography of your dance; you need to follow the steps to avoid stepping on anyone’s toes. Ensuring compliance isn’t just a legal obligation; it’s a demonstration of your commitment to responsible digital citizenship.
The Watchful Eye of Review
In the world of compliance, vigilance is your greatest ally. A regular review of your audit trail data is like keeping an eye on your financial statements for any unexpected transactions.
By consistently monitoring the data, you can swiftly detect any irregularities or unauthorized access attempts. Think of it as setting up security cameras to keep an eye on your digital premises.
The Compliance Orchestra: A Harmonious Symphony
In the grand orchestral performance of audit trail management, compliance is the conductor that ensures every instrument plays in harmony.
By adhering to regulations, securing your data, and maintaining an unwavering watch, you’re orchestrating a symphony of responsibility and transparency. You’re not just following the rules; you’re setting an example for ethical and accountable digital practices.
Remember that staying compliant isn’t just a checkbox on a to-do list; it’s a commitment to upholding the integrity of your internal procedures and digital operations.
By securely storing data, controlling access, and encrypting sensitive information, you’re ensuring that your audit trail remains a beacon of trustworthiness amidst the vast sea of data.
The core principles of audit trails are accountability and transparency. By upholding these principles, individuals and organizations can maintain trust, security, and responsible digital practices.
Workflow Automation Solution: Your Partner in Creating Perfect Audit Trails
As we delve deeper into the realm of audit trail mastery, let’s uncover a potent ally that can help us navigate this intricate landscape: workflow management software.
Think of it as a trusty sidekick on your internal audit adventure, aiding you in creating, managing, and safeguarding the digital footprints that shape your processes.
In this chapter, we’re unveiling the magic that workflow management software brings to the table.
Streamlining the Tracking Process
Picture this: you’re embarking on a treasure hunt, and each step you take leaves behind a mark. Workflow management software acts as your treasure map, automatically recording every action taken within your digital realm.
It’s like having a digital scribe chronicle your journey, ensuring no detail goes unnoticed. By seamlessly integrating with your processes, this software effortlessly captures the data needed to build a comprehensive audit trail.
Automating Timestamps and User Identification
Remember how Sherlock Holmes always kept a meticulous journal? Workflow management software does the same thing automatically. It stamps every action with a timestamp, noting the exact moment it occurred. This includes audit requests from the audit team.
Additionally, it identifies the users responsible for each action, providing a crystal-clear picture of who’s playing which role in your digital drama. It’s like having your audit trail data crafted by an invisible assistant, ensuring accuracy and transparency.
Activity Details Made Effortless
Every action within an existing process is like a scene in a play. Workflow management software doesn’t just note the scene; it describes it vividly. Did someone update a record? Add a comment? Approve a request?
This software captures the essence of each action, creating a comprehensive storyline. It’s as if a storyteller is narrating your audit trail, giving each event context and color.
Data Changes with Flair
In the evolution of data, each change is a pivotal moment. Workflow management software doesn’t just document these changes; it showcases them with flair.
Like a flipbook, it chronicles the data’s transformation over time, from its humble beginnings to its final form. This dynamic representation is invaluable for understanding the journey your data takes, akin to watching a caterpillar transform into a butterfly.
Security and Compliance: A Dynamic Duo
Imagine workflow management software as the vigilant guardian of your digital realm. It’s not just about recording actions; it’s also about securing them. This software incorporates security measures to protect your audit trail data from unauthorized access.
Encryption, authentication protocols, and role-based permissions create a fortress around your data, ensuring it remains inaccessible to anyone without proper clearance.
Unveiling Insights Through Analytics
Think of workflow management software as your data analyst, poring over the numbers to reveal hidden patterns. It’s not just about recording actions; it’s about interpreting them.
Through analytics, this software can provide insights into trends, anomalies, and efficiency bottlenecks. It’s like having a crystal ball that forecasts the future of your processes based on past actions.
A Dynamic Duo: Audit Trail and Workflow Software
As we traverse this realm of audit trail and workflow management, we realize that a workflow management solution is the perfect companion to our audit trail adventure.
It’s the bridge between actions and records, ensuring that your processes are seamlessly documented and secured.
By harnessing the power of this dynamic duo, you’re not just managing complex workflows; you’re crafting a comprehensive narrative of your digital journey.
Transform Your Business Processes with Flowster's AI-Driven Automation
Conclusion: Embracing the Odyssey of Audit Trail Mastery
In this digital era, where data flows like a river, audit trails stand as the rocks that guide and protect our journey.
They illuminate the path, ensuring accountability, transparency, and security in every action we take. With date and time stamps, user identifications, activity details, and data changes, audit trails paint a vivid picture of our digital landscape.
Creating and managing audit trails isn’t a mere obligation; it’s a testament to our commitment to responsible digital stewardship.
By reviewing, archiving, securing, and encrypting our data, we safeguard our digital legacy. Compliance becomes our compass, and regular vigilance ensures that our trail remains unblemished.
Let’s remember that audit trails are more than just records; they’re the legacy of our digital presence. Just as historians rely on well-preserved manuscripts, future generations will rely on our meticulously crafted audit trails to decipher the past.
By embracing the power of transparency, accountability, and security, we’re leaving a mark that transcends time and space.
Do you want to improve your business processes?
With Flowster, you can easily create standard operating procedures or work instructions by leveraging the power of AI, or you can browse our library of pre-built templates in the Flowster Marketplace.
Do you want assistance? Use our “Done for You” services to have our quality and improvement professionals create custom workflows for you.